Data masking is undeniably becoming more important for businesses than ever. Many companies suffer from data breaches, and even well-known organizations like H&M are fined millions for GDPR violations. For instance, in 2021, we saw the highest average recorded costs resulting from data breaches.
This goes to show how important it is to safeguard privacy-sensitive data against unauthorized access. Often, It can be a challenge with deep fake technology and more sophisticated cybercriminals out there.
Luckily, there are ways to tackle this issue and minimize data breaches due to advancements in technology. This article gives you insights into how businesses can leverage such technology for data masking to protect sensitive data.
What is data masking and what is it used for?
Data masking is often also known as anonymization or data redaction. In essence, it is a technique to safeguard sensitive data by masking it. You probably have seen either in series or movies classified government documents being blacklined or redacted. That is one of the applications of data masking.
As data privacy regulations and rules have gained more attention and priority, organizations need solutions to ensure compliance. This is mainly why data masking is used; to ensure compliance with data privacy regulations.
Let’s look at the types of sensitive data that often need masking next.
Types of data needed to be masked
There are various types of privacy-sensitive data that need to be well-protected from unauthorized access. The types of data that needed to be masked often fall under the following categories:
- Personally Identifiable Information (PII) – Data that can be used to identify or distinguish a person’s identity (e.g., name, Social Security Number, date of birth)

- Protected Health Information (PHI) – Data that refers to personal health information, both past and present (e.g., Medical Record Number, Social Security Number, health insurance beneficiary numbers)
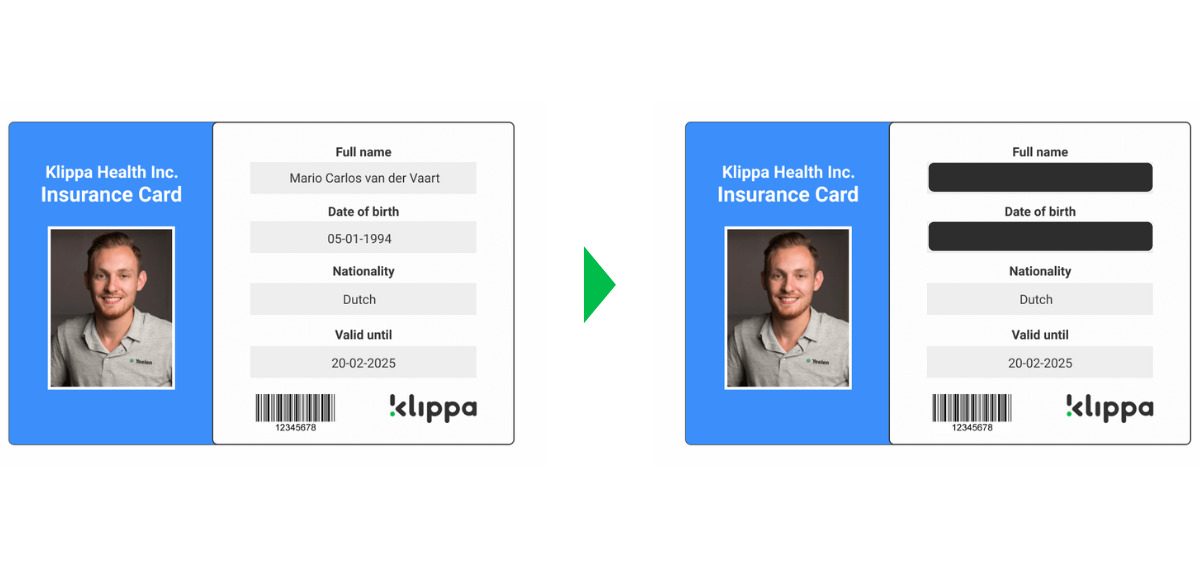
- Payment Card Information (PCI) – Data related to credit, debit, or other payment cards that can be used to identify a business or a customer (e.g., payment card numbers)

Now that we’ve got the types of sensitive data covered let’s jump into how data masking works.
How to mask data?
Traditionally, data and documents have been masked manually in the public sector and the legal industry. A technique often used is called data redaction, which you may know better as “blacklining”.
Take, for instance, the legal industry. For centuries, lawyers, paralegals, and back-office staff have been involved in redacting sensitive information from documents and court cases that have to be made available to the public.
They have been using markers to blackline information that is not allowed to be disclosed. In addition to blackline, it would require an additional person to check that redaction is done correctly. This, of course, takes valuable time from the lawyers and paralegals.
Although various software now helps organizations modify and blackline the documents in digital formats such as PDF, they are still not optimal when time and money are considered.
Thus, an automated solution for data masking is highly welcomed by businesses.
Automated data masking solution
The manual data masking method, such as document redaction, is often limited to human capabilities in terms of accuracy, efficiency, and consistency over time. Human mistakes are often unavoidable and can lead to immense financial losses.
The knowledgeable staff’s time is better dedicated to more critical tasks. Additionally, scalability is not even an option. Imagine adding more personnel to redact documents as the volume ramps up. The overhead costs would quickly rise to undesirable levels.
Hence Intelligent Document Processing (IDP) software was created; to make document processing and redaction easy for businesses. End-to-end solutions such as IDP software can automatically read the document, recognize the data fields, extract relevant information, and anonymize privacy-sensitive data within seconds.

But why would anyone be willing to trust technology to do that? This question can be best answered by listing the main benefits of an automated data masking solution.
Benefits of data masking automation
The reason why automating data masking has become widely adopted in multiple industries. It comes with many benefits, which include:
- Faster turnaround time
- Cost savings
- Data security
- Scalability
Faster turnaround time
With data masking automation, the turnaround time is significantly reduced. We move from the redaction speed of minutes to seconds per document.
When multiplying that by the number of documents, organizations can achieve a faster turnaround time, which can have a massive impact on business performance.
Cost savings
With software to automate data masking, less staff time is needed to dedicate to blacklining documents. This, in return, significantly reduces the overhead costs, which allows businesses to save money.
Additionally, faster turnaround times usually have a great impact on cost reduction as well.
Data security
With data masked and stored in a digital location, there are fewer risks of data being breached or accessed by unauthorized personnel. Even if the data were to be somehow breached, privacy-sensitive data would still remain protected.
Organizations would not need to store and archive a pile of documents in a physical location and risk the data being destroyed or leaked.
Scalability
Adding more staff and people to deal with the growing number of documents needed to be masked is simply too costly. Hence, manual document redaction is not a scalable solution for businesses.
With software that automates data masking, organizations can easily handle the growing number of documents or data. It is not restricted to anything other than hardware that can be updated when needed.
Securing data privacy with automation
The good thing is that the industry is still developing, and it’s not too late to start automating data masking. However, suppose your organization is looking to achieve business efficiency and safeguard privacy-sensitive data, we recommend taking action quickly. The faster you do it, the more beneficial it is for your business.