The digitalisation of global supply chains is unstoppable and there is no doubt about the upside potential it brings in terms of efficiency gains. Yet, the rapid progress in digital technologies, artificial intelligence, and data-driven decision-making exposes organisations to an elevated risk of systemic cyberattacks. And the material impact of cyber events such as the 2020 SolarWinds cyberattack in the US, as well as more recent incidents like XPlain and Concevis in Switzerland, highlights the interconnected nature of cyber threats within global supply chains, demanding increased attention from business leaders and policy makers. Against this backdrop, this article underscores the critical need for resilient cyber supply chain risk management (C-SCRM) practices across industry sectors, including those traditionally less associated with high-profile cyber threats.
Introduction to supply chain cyberattacks
The SolarWinds breach serves as a compelling case study, revealing the widespread consequences of vulnerabilities within supply chains. Drawing parallels with incidents in Switzerland, where the financial sector remains a prime target, this article aims to outline the complexities of safeguarding supply chains against evolving cyber threats.
While the Swiss financial sector has responded with comprehensive regulations, the spotlight shifts to broader industrial supply chains where similar regulations either do not exist or are not followed with adequate priority. Examining examples of supply chain cyberattacks on manufacturing companies unveils the vulnerabilities and challenges faced by these critical sectors.
In the United States, many industries have experienced targeted supply chain cyberattacks, disrupted operations, and compromised sensitive data. Recent incidents have illuminated the need for robust risk management strategies tailored to the unique characteristics of industrial supply chains. For example, in 2021, Colonial Pipeline, an oil pipeline system that carries jet fuels and petrol, encountered a ransomware attack that disrupted its operations, leading to a temporary shutdown. The focal point of the attack was the billing infrastructure, rather than the critical oil pumping systems, which remained operational. The decision to halt pipeline operations was attributed to the inability to bill customers. Colonial Pipeline took this precautionary measure to prevent potential further attacks on vulnerable sections of the pipeline, prompted by concerns that hackers might possess information enabling additional attacks. In a bid to restore network functionality, the company ultimately opted to pay a ransom of $4.4 million.
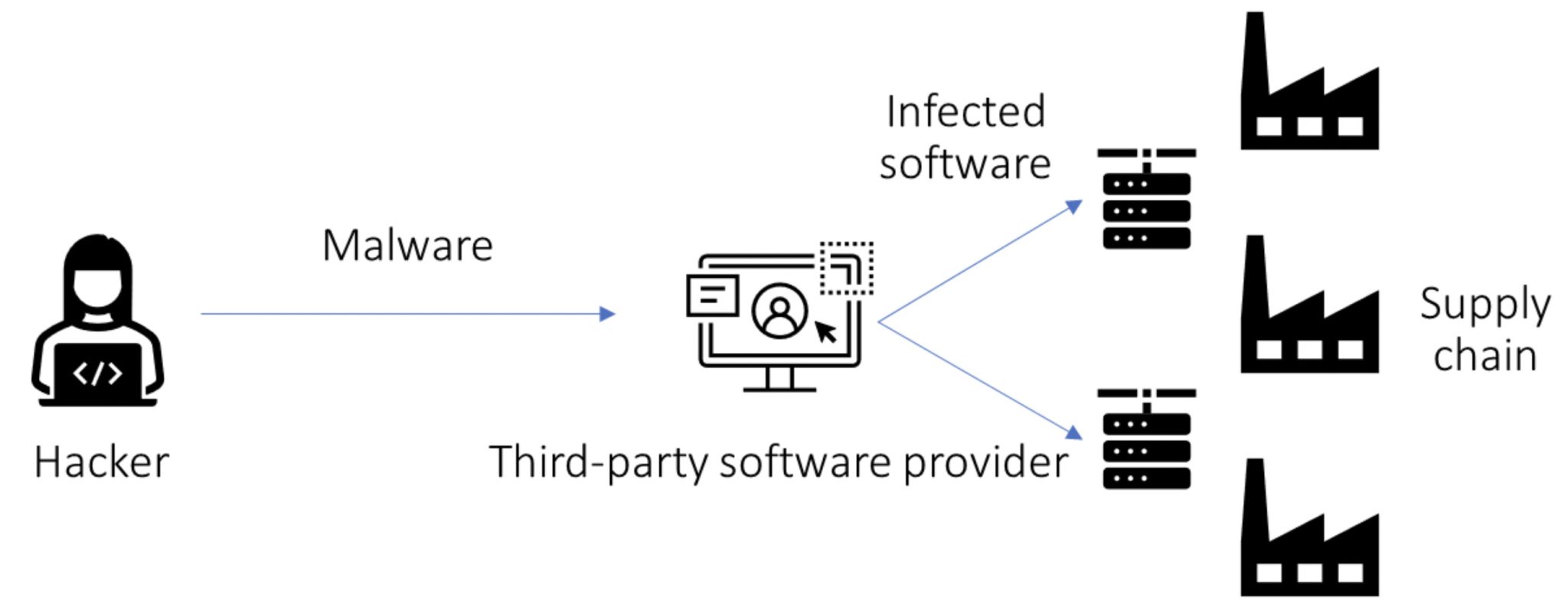
As depicted in figure 1, a typical supply chain attack focuses on a third-party software provider. The goal is to obtain unauthorized access to a larger network of suppliers and customers. The hackers achieve this by infiltrating the automated update servers of the targeted software provider. The pernicious aspect of such attacks lies in the fact that the affected companies, those relying on the software provider for updates, are often unaware that they are inadvertently installing malware onto their servers. Consequently, the malware can then spread throughout the network, potentially compromising the security of numerous interconnected organisations within the supply chain. This method allows the attackers to exploit the trust established between the targeted company and its software provider, using the update process as a Trojan horse to gain access to a more extensive supply chain network.
Hence, the lack of a proactive approach to C-SCRM can leave organisations and their supply chains susceptible to cyber risks, drawing attention to the importance of industry-wide collaboration, regulatory frameworks, and the adoption of international standards. And despite proven significance, the adoption of ISO certifications, such as ISO 27001, within industrial supply chains remains limited. This raises questions about the readiness of organisations to confront cyber risks head-on, especially in an era where cyber threats continue to evolve in sophistication. Furthermore, there are gaps in academic literature, necessitating action from both researchers and practitioners. This article underscores the imperative for a holistic approach to cybersecurity, in alignment with the evolving concept of cyber resilience.
Leveraging ISO standards and NIST frameworks for cyber supply chain risk management
In the intricate landscape of C-SCRM, two globally recognised frameworks – the ISO 27001 (International Organisation for Standardisation) standard1 and the NIST (National Institute of Standards and Technology) framework2 – play pivotal roles in guiding organisations toward robust risk management practices.
1. The ISO 27001 standard
While the ISO standards do not explicitly define C-SCRM as a standalone topic, the principles embedded in ISO 27001 provide valuable insights for managing risks associated with the buyer-supplier relationships. Key considerations within this standard advocate for comprehensive risk assessments along the entire supply chain. This necessitates a fundamental understanding of potential vulnerabilities and threats arising from supplier interactions.
Furthermore, the standards outline various security measures that organisations should implement to ensure information security. These measures offer flexibility, enabling adaptation to control risks associated with supplier interaction, and sensitive information exchange. Like customer relationship management, ISO 27001 recommends establishing clear security requirements and obligations in contracts or agreements with suppliers. This ensures adherence to security measures and compliance standards by both parties.
Regular monitoring and review of supplier and customer-related processes and security measures are crucial. This proactive approach enables organisations to swiftly identify potential risks or deviations from established security protocols.
Finally, robust incident response plans and business continuity measures mitigate risks arising from supplier-related incidents, minimising disruptions in operations.
While the term “C-SCRM” may not be explicitly detailed in ISO 27001, the principles of risk management, security controls, contractual obligations, and monitoring can be effectively applied to managing risks associated within the supply chain.
2. The NIST framework
NIST focuses on C-SCRM through various publications. However, the NIST Special Publication 800-161 deals with C-SCRM specifically. Key elements covered in NIST publications include guidelines for identifying, assessing, and managing risks within the supply chain, understanding potential vulnerabilities and threats throughout the supplier lifecycle.
The standard recommends evaluating and selecting suppliers based on their security practices, compliance with standards, and commitment to cybersecurity. It encourages information exchange and collaboration among supply chain stakeholders to effectively address and mitigate emerging threats. This may include sharing best practices, threat data, and security-related information.
The NIST approach to C-SCRM focuses on empowering organisations to establish comprehensive cybersecurity practices suited for dynamic and modern supply chains. Through detailed guidelines and recommendations, the NIST framework serves as a crucial tool for organisations to strengthen their capabilities in identifying, assessing, and effectively managing risks within their supply chain environment. The NIST framework outlines a range of factors fundamental for effective C-SCRM, with a particular emphasis on cultural and awareness-related components.
The role of insurance in cyber supply chain risk management
Cyber insurance can help businesses in several ways to manage cyber supply chain risk. First and foremost, it can provide reimbursement for losses incurred due to supply chain cyberattacks, such as data breach notification costs, regulatory fines, and business interruption losses. However, many cyber insurance providers offer risk assessment services to help businesses identify and address vulnerabilities in their supply chains. They may also provide access to cybersecurity experts who can assist in developing and implementing risk mitigation strategies. It can be used as a tool to incentivise suppliers to adopt stronger cybersecurity practices. Businesses can require suppliers to carry cyber insurance and meet certain cybersecurity standards as a condition of doing business.
When selecting cyber insurance coverage, businesses should consider several factors, including the size and complexity of their supply chain, the type of data and assets stored or transmitted within the supply chain, the industry they operate in, and their overall cybersecurity posture.
Cyber insurance is an essential component of a comprehensive supply chain risk management strategy. By providing financial protection, risk assessment services, and contractual leverage, cyber insurance can help businesses mitigate the impact of supply chain cyberattacks and protect their bottom line. As cyber threats continue to evolve, businesses must adopt cyber insurance as a strategic shield to safeguard their supply chains and ensure business continuity. Major insurance companies offer tailored cyber risk coverage that is accessible to both global organisations and SMEs.
Best practices for implementing a C-SCRM programme
In the intricate realm of cyber threats within the supply chain, organisations can bolster their defences by adopting a comprehensive C-SCRM programme. These practices, combined with the seven steps outlined in table 1, offer a roadmap for safeguarding the supply chain and effectively managing cyber risks associated with suppliers.
Table 1. The seven steps to kick-start your C-SCRM programme.
| Step | Description | Implementation |
| 1 | Select a comprehensive risk management framework | Choose a robust framework, such as NIST, to structure your C-SCRM programme. Tailor it to the specific nuances of your supply chain.
|
| 2 | Conduct in-depth supplier risk assessment | Perform a detailed risk analysis to identify and understand cyber risks associated with each supplier in the supply chain. Consider factors such as their cybersecurity posture, data handling practices, and overall risk exposure.
|
| 3 | Define your supply chain risk appetite
|
Clearly articulate your organisation’s risk appetite levels, ensuring alignment with the diverse risks posed by different suppliers in the supply chain. Embrace economic supply chain risk capital as your compass to guide strategic decisions.
|
| 4 | Develop strategic mitigation plans with key suppliers | Collaborate with suppliers to develop strategic risk mitigation plans, focusing on proactive measures to minimise potential impacts on the supply chain.
|
| 5 | Institute minimum cybersecurity standards across the supply chain | Prioritise basic cybersecurity practices throughout the supply chain. Establish monitoring mechanisms, baseline behaviours, and multi-layered defence systems to mitigate risks collectively.
|
| 6 | Ensure supplier-driven backup and recovery protocols | Collaborate with suppliers to establish robust backup procedures that are regularly tested and encrypted. Ensure that backup media are stored securely, avoiding proximity to operational systems. |
| 7 | Strategically integrate cyber insurance for supply chain resilience
|
Leverage cyber insurance in collaboration with suppliers. Align it with risk management frameworks and use it as a supplementary tool for financial protection, risk assessment, and contractual leverage within the supply chain. |
On a more technical note, initiating the process with a basic cybersecurity questionnaire for suppliers or harnessing the latest technologies, such as incorporating external cyber risk scores from firms like OneTrust or SecurityScorecard, can significantly streamline the risk assessment process. This is particularly beneficial for companies dealing with a multitude of suppliers, providing a more efficient and comprehensive approach to evaluating and managing cyber risks across a broad supplier base. Alternatively, collaborating with supplier risk assessment partners like GRMS, who provide tailored solutions and supply chain risk analysis capabilities, is another effective approach.
Conclusion – your supplier’s cyber risks are your risks
The examples of cyberattacks, such as the one on SolarWinds in 2020 and similar incidents in Switzerland in 2023, underscore the necessity of improving cybersecurity in buyer-supplier relationships.
The holistic approach outlined in this article, focusing on collaborative risk management, fundamental cyber hygiene, and the strategic integration of cyber insurance, empowers organisations to fortify their supply chain resilience against evolving cyber threats. By actively engaging with suppliers, businesses can create a robust line of defence that protects the entire supply chain ecosystem from potential cyber attacks. The imperative remains unwavering – implement known strategies to safeguard the intricate web of the digital supply chain ecosystem.
About the Author
Dr. Kamil J. Mizgier is the former Global Supplier Relationship and Risk Management Leader at Dow with 15 years of experience in implementing risk management strategies across industry sectors. Before this role, he led enterprise risk modelling projects and teams, among others, at BNY Mellon and UBS. He has published more than twenty academic and practitioner journal articles on risk management and is a frequent public speaker. He obtained his master’s degree in applied physics at the Warsaw University of Technology and a PhD in supply chain management at ETH Zurich.
References:
- Boyens, J., Smith, A., Bartol, N., Winkler, K., Holbrook, A., & Fallon, M. (Oct, 2021). Cybersecurity Supply Chain Risk Management Practices for Systems and Organizations. (N. I. Technology), access https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-161r1-draft2.pdf
- International Standard ISO/IEC 27001. (Jan. 2022). Information security, cybersecurity and privacy protection – Information security management systems – Requirements (Third edition 2022-10), access https://www.iso.org/standard/27001